Needtoknow Principle in der ITSicherheit

Business Need To Know Principle BISUNIS
Need-to-Know Principle. This video lesson provides a short refresher on the fundamental Need-to-Know security principle. It reviews two case histories and provides guidelines on your responsibilities for applying the principle. The lesson also includes training resources on how to identify insider threats that may be violating the Need-to-Know.

São Tomé and Príncipe everything you need to know before you visit I'M 8 HOURS AHEAD Sao
The Need-to-know principle may require much more diligence and particularly different procedures than the often used discretionary or role-based access control - as under Windows Server, the Azure RBAC system or SQL Server. This depends on the exact implementation of the Need-to-know factor within the system. When a user changes job roles it.

Needtoknow Principle in der ITSicherheit
1. The SECRET classification tier is used for sensitive information that requires enhanced protective controls, the use of appropriately assured IT (such as the Rosa capability provisioned to most.

Business Need To Know Principle BISUNIS
The need-to-know principle must be strictly enforced for access to international partners' information. 21. How the UK provides classified information to international partners,.

5 Learning Principles L&D Professionals Need To Know Infographic eLearning Infographics
The term " need to know ", when used by governments and other organizations (particularly those related to military or espionage ), describes the restriction of data which is considered very confidential and sensitive. Under need-to-know restrictions, even if one has all the necessary official approvals (such as a security clearance) to access.
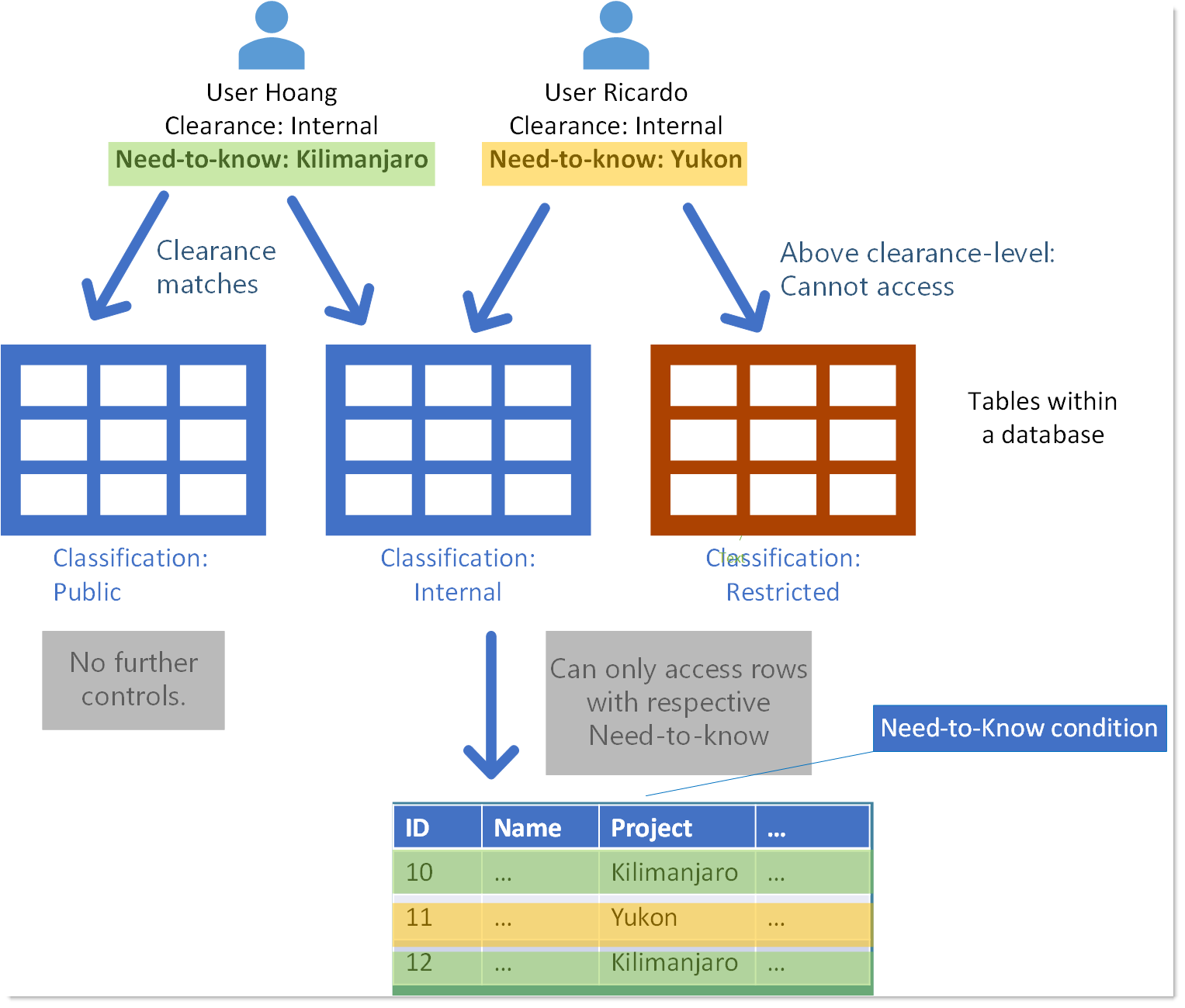
Security The Needtoknow principle Microsoft Tech Community
Wikipedia

Figure 1 from "Needtoknow" principle and fuzzy security clearances modelling Semantic Scholar
Implementing the need to know principle ensures that individuals only have access to the information that is necessary for them to perform their job duties, reducing the risk of sensitive data falling into the wrong hands. On the other hand, the least privilege principle minimizes the risk of unauthorized access by granting individuals the.
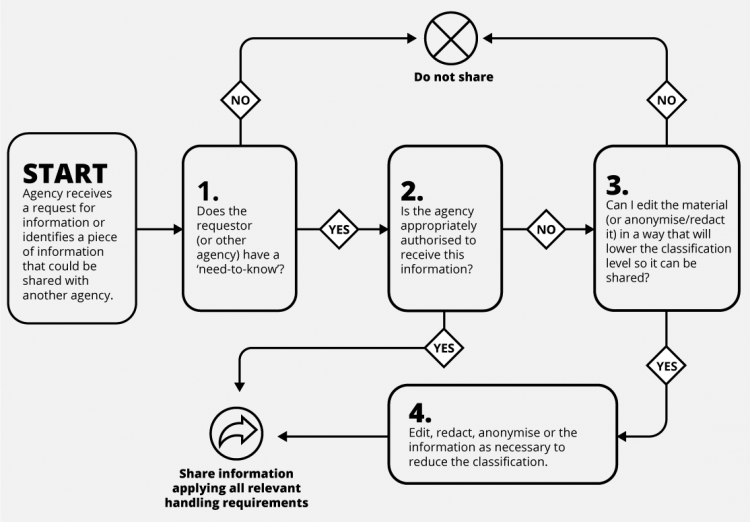
Controlling access to information Protective Security Requirements
Need To Know Principle. The need to know principle can be enforced with user access controls and authorisation procedures and its objective is to ensure that only authorised individuals gain access to information or systems necessary to undertake their duties.
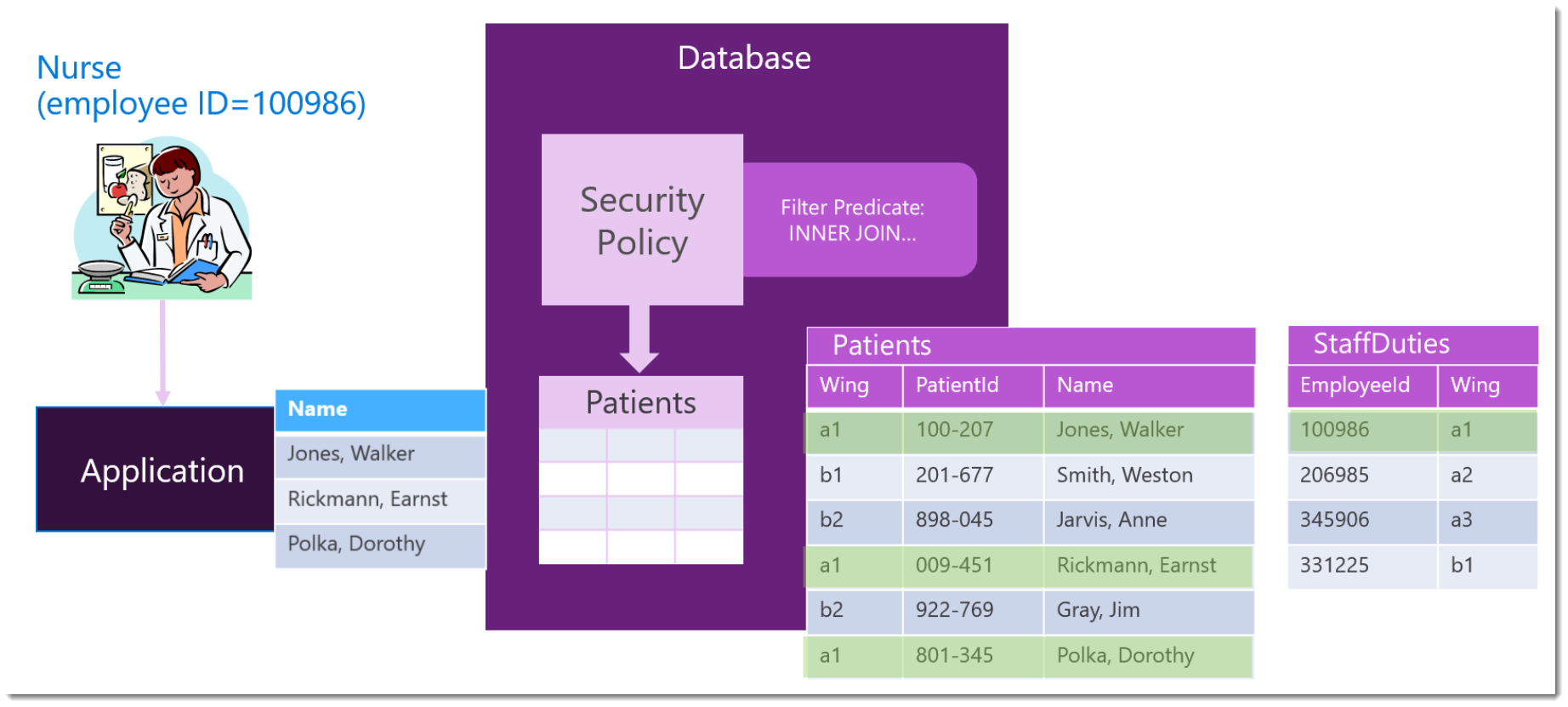
Security The Needtoknow principle Microsoft Community Hub
"The need-to-know principle combines data security with the economy of knowledge. It relieves the burden on users, administrators and compliance departments alike," explains Andrea Wörrlein, Managing Director of VNC in Berlin and member of the Board of VNC AG in Zug. "Users only get access to information that is relevant to them.

[PDF] "Needtoknow" principle and fuzzy security clearances modelling Semantic Scholar
need-to-know. Definitions: A determination within the executive branch in accordance with directives issued pursuant to this order that a prospective recipient requires access to specific classified information in order to perform or assist in a lawful and authorized governmental function. Sources: CNSSI 4009-2015 from E.O. 13526. Decision made.

UI Data Protection Applying the “Need to Know” Principle in SAP S/4HANA Defense & Security
Unlike the principle of need to have available, the need-to-know principle assumes data are available independent of the task at hand. This becomes more granular with the principle of need to have available, which focuses on what data are required for performing specific tasks at any given time (figure 1).

Needtoknow Principle in der ITSicherheit
requirement to reinforce the 'need to know' principle but that can be managed on OFFICIAL (rather than SECRET) systems and infrastructure with additional safeguards (usually procedural rather than technical). 4.2 Examples of appropriate use of OFFICIAL-SENSITIVE may include (but are not limited .

PPT CSC 405 Introduction to Computer Security PowerPoint Presentation ID565469
The need to know principle shall be rigorously enforced for this information, particularly where it might be shared outside of a routine or well understood business process. There are very few activities where all related information or cases require the Official-Sensitive marking, though this might apply to assets previously marked as CONFIDENTIAL .

Security The Needtoknow principle Microsoft Community Hub
Principle 7: The duty to share information for individual care is as important as the duty to protect patient confidentiality. Health and social care professionals should have the confidence to.

Business Need To Know Principle BISUNIS
Let's say James Bond has "secret" clearance. That's his privilege. Should he have "top secret"? No. For a variety of reasons, even though he's James Bond, he has the least privilege he needs: He doesn't need to know "top secret" things, so his (least) privilege level is set to "secret."

Implementing the NeedToKnow principle >>Redlings
The need-to-know principle underpins decision making on OFFICIAL information. The information creator is responsible for determining whether a recipient needs-to-know; access to OFFICIAL.